Listen up, tech enthusiasts! If you're diving into the world of IoT and remote access, you're going to need a crash course on RemoteIoT platform SSH key. This isn't just any tech jargon; it's your golden ticket to secure connections in the digital age. Whether you're a developer, system admin, or just someone curious about how the tech world keeps things safe, this guide is your go-to resource. So, buckle up and let's dive deep into the realm of RemoteIoT SSH keys.
Now, you might be thinking, "Why all the fuss about SSH keys?" Well, in a world where cyber threats are lurking around every corner, having a secure connection is non-negotiable. RemoteIoT platform SSH key plays a crucial role in ensuring that your devices and data stay safe while you access them from anywhere in the world. It's like having a digital bouncer at the door, letting only the right people in.
But don't just take my word for it. As we journey through this article, you'll uncover the ins and outs of SSH keys, their importance in the RemoteIoT platform, and how they can revolutionize the way you manage your IoT devices. So, whether you're a seasoned pro or just starting out, there's something here for everyone.
Read also:Hilary Farr Children A Closer Look At Her Family Life And Journey
What Exactly is a RemoteIoT Platform SSH Key?
Alright, let's break it down. An SSH key is essentially a pair of cryptographic keys that allow secure communication between two systems. In the context of the RemoteIoT platform, these keys act as a digital passport, ensuring that only authorized users can access your IoT devices remotely. Think of it as a secret handshake that only you and your device know.
Here's the kicker: unlike traditional passwords, SSH keys are way harder to crack. They use complex algorithms that make brute-force attacks practically impossible. So, if you're looking for a foolproof way to secure your IoT setup, SSH keys are your best bet.
Why Should You Care About SSH Keys in RemoteIoT?
Here's the deal: the Internet of Things is growing faster than ever. With billions of devices connected worldwide, the risk of unauthorized access is higher than ever. That's where SSH keys come in. They provide an additional layer of security that traditional methods just can't match.
Let's face it, no one wants to wake up to a news headline about their smart home being hacked. By implementing SSH keys in your RemoteIoT platform, you're taking a proactive step towards safeguarding your digital assets. Plus, it's not just about security; it's about peace of mind knowing your data is in safe hands.
How Do SSH Keys Work in RemoteIoT?
Alright, let's get technical for a moment. When you set up an SSH key pair, you get two keys: a private key and a public key. The public key is shared with your RemoteIoT platform, while the private key stays safely tucked away on your device. When you try to access your IoT device remotely, the platform uses the public key to verify your identity by checking it against your private key.
Here's a quick breakdown of the process:
Read also:Lori Petty Wife The Fascinating Journey Of Robin Wright
- Generate an SSH key pair using a tool like OpenSSH.
- Upload the public key to your RemoteIoT platform.
- Store the private key securely on your local machine.
- Use the private key to authenticate whenever you need remote access.
It's like a digital handshake that ensures only you can unlock the door to your IoT devices.
Benefits of Using SSH Keys in RemoteIoT
So, why should you bother with SSH keys when passwords have worked just fine for years? Here's a rundown of the benefits:
Enhanced Security
SSH keys offer a significantly higher level of security compared to passwords. With their complex encryption algorithms, they make it nearly impossible for hackers to gain unauthorized access.
Convenience
Once set up, SSH keys eliminate the need to remember long, complicated passwords. You can simply use your private key to authenticate, making the login process faster and more efficient.
Scalability
As your IoT network grows, managing multiple devices becomes a breeze with SSH keys. You can easily add or remove keys as needed, ensuring that your setup remains secure and manageable.
Reliability
SSH keys are less prone to human error compared to passwords. No more worrying about typos or forgotten credentials. It's all about seamless, reliable access.
Setting Up SSH Keys for Your RemoteIoT Platform
Ready to get started? Here's a step-by-step guide to setting up SSH keys for your RemoteIoT platform:
Step 1: Generate Your SSH Key Pair
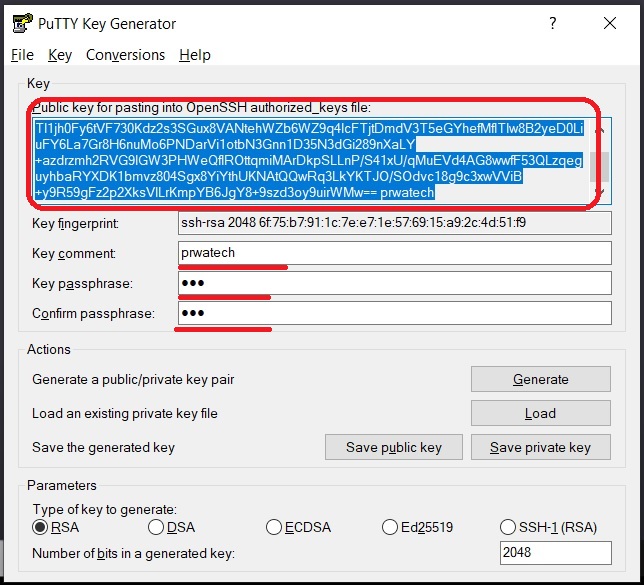
First things first, you'll need to generate your SSH key pair. On most systems, you can do this using the ssh-keygen command. Just open your terminal and type:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This will create a key pair with your email as a label. Easy peasy, right?
Step 2: Upload Your Public Key
Next, you'll need to upload your public key to your RemoteIoT platform. This process may vary depending on your platform, but generally, you'll find an option to add SSH keys in your account settings.
Step 3: Secure Your Private Key
Now, it's time to secure your private key. Make sure it's stored in a safe location and protected with a strong passphrase. This key is your golden ticket, so treat it like one.
Step 4: Test Your Connection
Finally, test your connection to ensure everything is working as expected. Try accessing your IoT device remotely using your SSH key. If all goes well, you should be good to go!
Common Challenges and How to Overcome Them
Like any technology, SSH keys come with their own set of challenges. Here are some common issues you might face and how to tackle them:
Lost Private Key
If you lose your private key, don't panic. Simply generate a new key pair and upload the public key to your RemoteIoT platform. Just make sure to revoke the old key to prevent unauthorized access.
Key Expiration
Some platforms have expiration dates for SSH keys. Be sure to check your platform's settings and renew your keys as needed to avoid any disruptions.
Key Management
As your IoT network grows, managing multiple keys can become a challenge. Consider using a key management tool to keep everything organized and secure.
Best Practices for SSH Key Management
To ensure your SSH keys remain secure and effective, follow these best practices:
- Use strong, unique passphrases for your private keys.
- Regularly review and revoke unused or compromised keys.
- Limit the number of keys you generate to reduce the risk of exposure.
- Store your private keys in a secure location, such as a hardware security module (HSM).
By following these guidelines, you'll keep your RemoteIoT platform SSH keys in tip-top shape.
Real-World Applications of RemoteIoT Platform SSH Keys
Now that you know the ins and outs of SSH keys, let's explore some real-world applications:
Smart Home Automation
With SSH keys, you can securely manage your smart home devices from anywhere in the world. Whether you're adjusting the thermostat or checking your security cameras, SSH ensures your connection remains secure.
Industrial IoT
In industrial settings, SSH keys are used to secure communication between machines and control systems. This ensures that critical infrastructure remains protected from cyber threats.
Healthcare IoT
For healthcare providers, SSH keys provide a secure way to access patient data and medical devices remotely. This is crucial in maintaining patient privacy and ensuring compliance with regulations like HIPAA.
Future Trends in RemoteIoT Platform SSH Keys
As technology continues to evolve, so too will the role of SSH keys in the RemoteIoT platform. Here are some trends to watch out for:
Quantum-Resistant Algorithms
With the rise of quantum computing, researchers are developing new algorithms that can withstand attacks from quantum computers. Expect SSH keys to adopt these advancements in the near future.
AI-Driven Key Management
Artificial intelligence is revolutionizing key management by automating tasks like key rotation and revocation. This will make SSH key management more efficient and secure.
Blockchain Integration
Blockchain technology is being explored as a way to enhance the security of SSH keys. By storing keys on a decentralized ledger, it becomes nearly impossible for hackers to tamper with them.
Conclusion
And there you have it, folks! A comprehensive guide to RemoteIoT platform SSH keys. From understanding what they are to implementing them in your IoT setup, you're now equipped with the knowledge to secure your digital world. Remember, security isn't just a feature; it's a necessity in today's connected age.
So, what are you waiting for? Take action and start securing your RemoteIoT platform with SSH keys. Share this article with your tech-savvy friends and let's spread the word about the importance of digital security. Together, we can build a safer, smarter IoT ecosystem.
Table of Contents
- RemoteIoT Platform SSH Key: Your Ultimate Guide to Secure Remote Access
- What Exactly is a RemoteIoT Platform SSH Key?
- Why Should You Care About SSH Keys in RemoteIoT?
- How Do SSH Keys Work in RemoteIoT?
- Benefits of Using SSH Keys in RemoteIoT
- Enhanced Security
- Convenience
- Scalability
- Reliability
- Setting Up SSH Keys for Your RemoteIoT Platform
- Step 1: Generate Your SSH Key Pair
- Step 2: Upload Your Public Key
- Step 3: Secure Your Private Key
- Step 4: Test Your Connection
- Common Challenges and How to Overcome Them
- Best Practices for SSH Key Management
- Real-World Applications of RemoteIoT Platform SSH Keys
- Future Trends in RemoteIoT Platform SSH Keys
- Conclusion