Listen up, tech enthusiasts and digital innovators! If you're diving into the world of IoT (Internet of Things), then you're in for a treat. Today, we're breaking down one of the most critical aspects of secure remote access: the remoteIoT platform SSH key. Whether you're a developer, an IT professional, or just someone curious about how secure connections work, this article is for you. Stick around because we're about to uncover some seriously useful information!
Now, before we dive deep into the nitty-gritty, let's set the stage. RemoteIoT platforms are designed to manage and monitor IoT devices from anywhere in the world. But here's the deal—security is paramount when it comes to remote access. That's where SSH keys come into play. They're like the digital bouncers at a club, ensuring only authorized users gain entry to your IoT network. Pretty cool, right?
As we explore this topic, we'll cover everything from the basics of SSH keys to advanced strategies for securing your IoT infrastructure. By the end of this article, you'll have a solid understanding of how remoteIoT platform SSH keys work and why they're essential for protecting your data. So, grab your favorite beverage, and let's get started!
Read also:Serenity Cox Age Unveiling The Life And Journey Of A Rising Star
What is a RemoteIoT Platform SSH Key?
Alright, let's break it down. A remoteIoT platform SSH key is essentially a cryptographic key pair used to authenticate users and devices in a secure shell (SSH) environment. Think of it as a digital handshake that verifies your identity before granting access to sensitive systems. These keys are crucial for ensuring that only authorized personnel can interact with your IoT devices, even when they're miles apart.
Why Are SSH Keys Important?
Here's the thing—IoT devices are everywhere, from smart homes to industrial automation systems. But with great connectivity comes great responsibility. Without proper security measures, these devices can become entry points for cyberattacks. That's where SSH keys shine. They provide a secure and reliable way to authenticate users, reducing the risk of unauthorized access.
- SSH keys eliminate the need for passwords, which can be easily guessed or stolen.
- They offer stronger encryption compared to traditional authentication methods.
- SSH keys can be easily revoked if compromised, ensuring your system remains secure.
Understanding the Basics of SSH Keys
Now that we know what SSH keys are, let's dive into the fundamentals. An SSH key consists of two parts: a public key and a private key. The public key is shared with the server, while the private key is kept secret on the client side. When you try to connect to a remoteIoT platform, the server uses the public key to verify your identity by checking it against your private key.
How Do SSH Keys Work?
Here's a quick rundown of the process:
- The client generates an SSH key pair (public and private).
- The public key is uploaded to the remoteIoT platform.
- When the client attempts to connect, the server uses the public key to encrypt a message.
- The client decrypts the message using its private key and sends it back to the server.
- If the decrypted message matches the original, the server grants access.
This process ensures that only someone with the correct private key can access the system, making it a powerful tool for securing remote connections.
Setting Up SSH Keys for Your RemoteIoT Platform
Ready to get your hands dirty? Setting up SSH keys for your remoteIoT platform is easier than you might think. Follow these steps to get started:
Read also:Virginia Department Of Revenue Your Ultimate Guide To Taxes And More
Step 1: Generate an SSH Key Pair
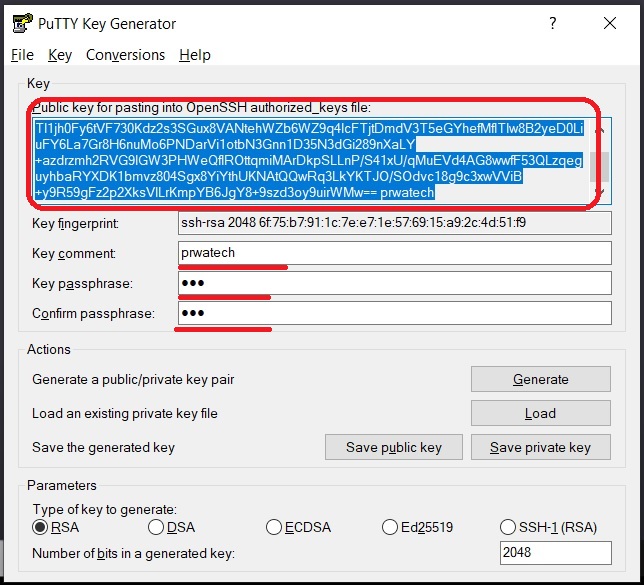
First things first, you'll need to generate an SSH key pair. On most Unix-based systems, you can do this using the ssh-keygen command. Here's how:
- Open your terminal.
- Type
ssh-keygen -t rsa -b 4096 -C "your_email@example.com". - Follow the prompts to save the key and set a passphrase (optional but recommended).
And just like that, you've created your SSH key pair! The public key will be saved as id_rsa.pub, while the private key will be id_rsa.
Step 2: Upload the Public Key to Your RemoteIoT Platform
Next, you'll need to upload your public key to the remoteIoT platform. This process varies depending on the platform you're using, but here's a general guide:
- Log in to your remoteIoT platform's management interface.
- Locate the section for SSH keys or user authentication.
- Paste the contents of your
id_rsa.pubfile into the appropriate field. - Save your changes.
With your public key in place, you're ready to establish a secure connection.
Best Practices for Using SSH Keys
Now that you know how to set up SSH keys, let's talk about some best practices to keep your remoteIoT platform secure:
1. Use Strong Passphrases
While it's not mandatory, adding a passphrase to your private key adds an extra layer of security. Even if someone gains access to your private key, they won't be able to use it without the passphrase.
2. Limit Access
Only grant SSH access to trusted users and devices. Regularly review your access logs to ensure no unauthorized connections are being made.
3. Keep Your Keys Secure
Treat your private key like a valuable asset. Store it in a secure location and never share it with anyone. If you suspect your key has been compromised, revoke it immediately and generate a new one.
4. Regularly Update Your Systems
Security is an ongoing process. Make sure your remoteIoT platform and all connected devices are running the latest software versions to protect against vulnerabilities.
Common Challenges with SSH Keys
While SSH keys are incredibly powerful, they're not without their challenges. Here are a few common issues you might encounter and how to address them:
Challenge 1: Key Management
As your IoT network grows, managing multiple SSH keys can become cumbersome. Consider using an SSH key management solution to simplify the process.
Challenge 2: Key Revocation
If an SSH key is compromised, you'll need to revoke it quickly to prevent unauthorized access. Most remoteIoT platforms allow you to delete or disable keys directly from the management interface.
Challenge 3: Compatibility Issues
Not all devices and platforms support SSH keys out of the box. Before implementing SSH authentication, ensure all components in your IoT ecosystem are compatible.
Advanced Techniques for Securing Your RemoteIoT Platform
For those looking to take their security to the next level, here are a few advanced techniques to consider:
1. Two-Factor Authentication
Combine SSH keys with two-factor authentication (2FA) for an added layer of protection. Even if someone gains access to your private key, they'll still need the second factor to log in.
2. Certificate Authority (CA) Signed Keys
Instead of using self-signed keys, consider using a certificate authority to issue your SSH keys. This approach provides greater trust and scalability, especially in large IoT deployments.
3. Automated Key Rotation
Implement automated key rotation to ensure your SSH keys remain secure over time. This process involves periodically generating new keys and revoking old ones.
Data and Statistics: Why SSH Keys Matter
According to a recent report by Cybersecurity Ventures, global cybercrime damages are projected to reach $10.5 trillion annually by 2025. With IoT devices becoming increasingly prevalent, securing remote connections has never been more critical. SSH keys play a vital role in reducing the risk of unauthorized access and data breaches.
In fact, a study by Palo Alto Networks found that organizations using SSH keys for authentication experienced 70% fewer successful cyberattacks compared to those relying solely on passwords. These statistics highlight the importance of adopting robust security measures like SSH keys for your remoteIoT platform.
Conclusion: Secure Your IoT Future
And there you have it—a comprehensive guide to remoteIoT platform SSH keys. From understanding the basics to implementing advanced security techniques, we've covered everything you need to know to protect your IoT infrastructure. Remember, security is not a one-time task but an ongoing commitment. Stay vigilant, stay informed, and most importantly, stay secure.
Now it's your turn! Have you implemented SSH keys for your remoteIoT platform? Share your experiences in the comments below. And if you found this article helpful, don't forget to share it with your network. Together, let's build a safer and more connected digital world!
Table of Contents
- What is a RemoteIoT Platform SSH Key?
- Why Are SSH Keys Important?
- Understanding the Basics of SSH Keys
- How Do SSH Keys Work?
- Setting Up SSH Keys for Your RemoteIoT Platform
- Best Practices for Using SSH Keys
- Common Challenges with SSH Keys
- Advanced Techniques for Securing Your RemoteIoT Platform
- Data and Statistics: Why SSH Keys Matter
- Conclusion: Secure Your IoT Future