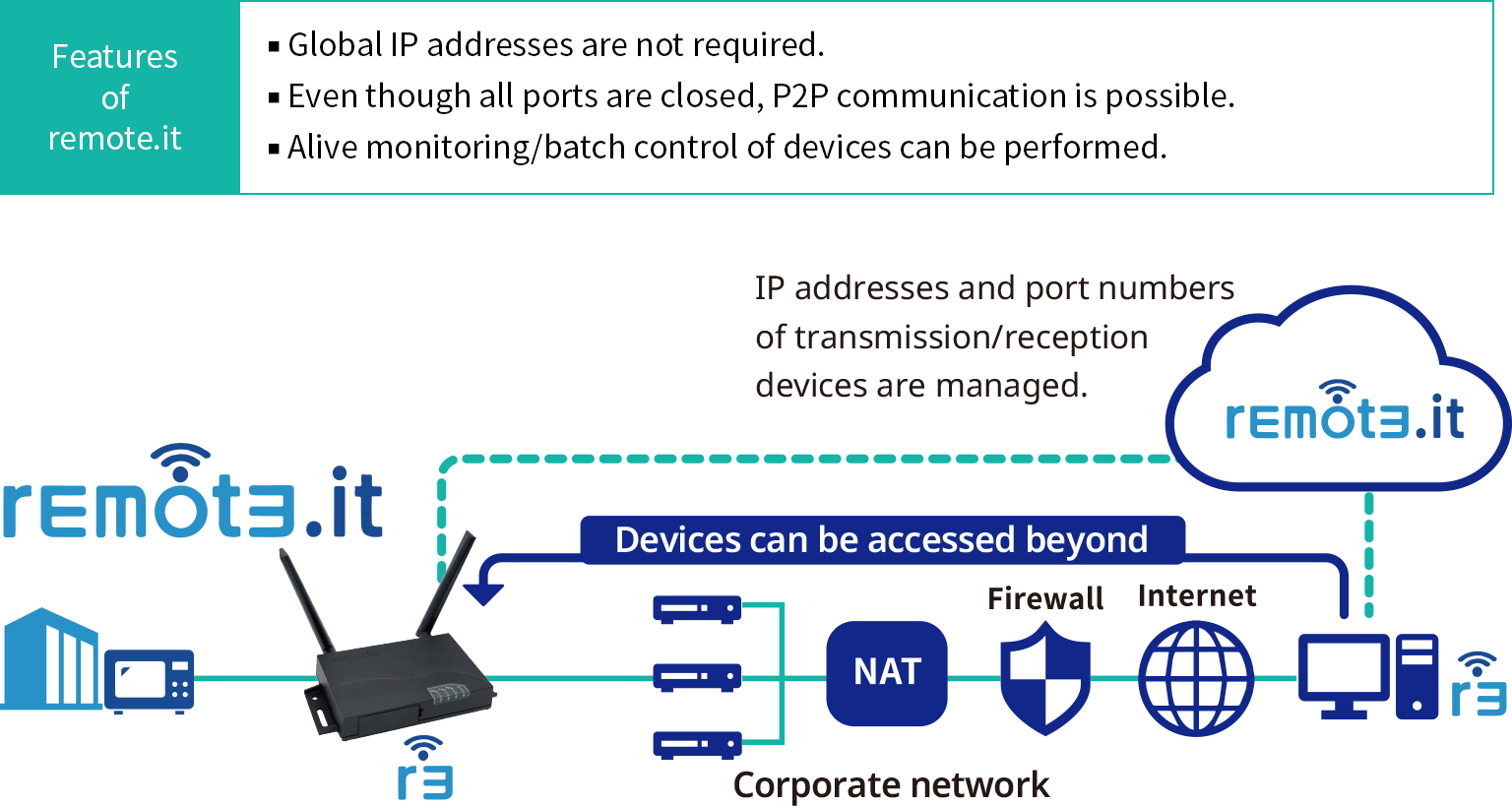
Picture this: You’re chilling on your couch, scrolling through your smart home devices, and suddenly you realize you can’t connect to one of them remotely. Frustrating, right? But don’t sweat it because today, we’re diving deep into the world of IoT remote access behind router MAC. Yep, you heard that right. We’re talking about how to securely and efficiently manage your IoT devices from anywhere in the world, even when they’re tucked behind your router’s MAC address. So, grab your coffee, and let’s get started!
In this digital age, IoT devices have become an essential part of our lives. From smart thermostats to security cameras, these gadgets make our lives easier, but they also come with their own set of challenges. One of the biggest hurdles is accessing them remotely without compromising security. That’s where understanding IoT remote access behind router MAC comes into play. It’s like having a secret passageway to your smart home, no matter where you are.
This guide isn’t just about theory; it’s about practical solutions that work. Whether you’re a tech-savvy individual or someone who’s just starting to explore the IoT world, this article has got you covered. By the end of it, you’ll be able to set up and manage your IoT devices like a pro, ensuring they’re both accessible and secure. So, buckle up because we’re about to embark on a tech-savvy journey!
Read also:St Louis Cardinals Game Schedule Your Ultimate Guide For Baseball Fans
What is IoT Remote Access Anyway?
Let’s break it down. IoT remote access is essentially the ability to control and monitor your Internet of Things devices from afar. Think of it as giving your devices a virtual handshake, allowing you to interact with them even when you’re not physically present. It’s super convenient, especially if you’re the type who likes to check in on your home while you’re on vacation or at work.
Now, when we talk about IoT remote access behind router MAC, we’re referring to accessing these devices while they’re connected to a local network that’s protected by a router’s MAC address filtering. This adds an extra layer of security, making it harder for unauthorized users to gain access. But hey, with great power comes great responsibility, so we’ll also be discussing how to ensure your setup remains secure.
Here’s a quick rundown of why IoT remote access is a game-changer:
- Convenience: Control your devices from anywhere in the world.
- Security: Implement robust security measures to protect your devices.
- Efficiency: Streamline your smart home management and save time.
Why Router MAC Matters in IoT Remote Access
Alright, let’s talk about the elephant in the room – router MAC. Your router’s MAC address is like its fingerprint. It’s a unique identifier that helps differentiate it from other devices on the network. When you’re setting up IoT remote access, understanding how your router’s MAC address works can be a game-changer.
For starters, MAC filtering allows you to specify which devices are allowed to connect to your network. This means that even if someone tries to access your network remotely, they won’t be able to unless their device’s MAC address is on the approved list. It’s like having a bouncer at a club – only the right people get in.
Here’s the kicker though – MAC filtering isn’t foolproof. Savvy hackers can spoof MAC addresses, so it’s important to combine it with other security measures. But don’t worry, we’ll cover that in the next section. For now, just know that your router’s MAC address is a crucial piece of the IoT remote access puzzle.
Read also:Lori Petty Wife The Fascinating Journey Of Robin Wright
Setting Up IoT Remote Access
Step 1: Understand Your Network
Before you dive headfirst into setting up IoT remote access, it’s important to understand your network setup. This includes knowing your router’s IP address, MAC address, and any firewalls that might be in place. Think of it as mapping out the terrain before you go on an adventure – it’ll save you a lot of trouble later on.
Step 2: Configure Port Forwarding
Port forwarding is like creating a direct line to your IoT device. It allows you to bypass your router’s firewall and access your device remotely. Here’s how you do it:
- Log in to your router’s admin panel.
- Find the port forwarding section and add a new rule.
- Specify the port number and the IP address of your IoT device.
It might sound complicated, but once you get the hang of it, it’s pretty straightforward. Just remember to keep your port numbers secure and avoid using common ones like 80 or 22.
Step 3: Secure Your Connection
Security should always be your top priority when setting up IoT remote access. Here are a few tips to keep your devices safe:
- Use strong, unique passwords for all your devices.
- Enable two-factor authentication whenever possible.
- Regularly update your firmware and software to patch any vulnerabilities.
Common Challenges and How to Overcome Them
Setting up IoT remote access isn’t always smooth sailing. You might encounter a few bumps along the way, but don’t worry – we’ve got you covered. Here are some common challenges and how to overcome them:
- Connection Issues: Make sure your router is properly configured and that your devices are connected to the correct network.
- Security Breaches: Regularly monitor your network for any suspicious activity and update your security measures accordingly.
- Compatibility Problems: Ensure that all your devices are compatible with your network and that they’re using the latest firmware.
Best Practices for IoT Remote Access
Now that you’ve got the basics down, let’s talk about best practices. These tips will help you maximize the potential of your IoT remote access setup:
- Always use a secure connection, preferably over HTTPS or SSH.
- Limit the number of devices that can access your network remotely.
- Regularly review your network settings and make adjustments as needed.
By following these best practices, you’ll not only improve the performance of your IoT devices but also enhance their security. It’s a win-win situation!
Understanding the Security Risks
Security is a big deal when it comes to IoT remote access. If you’re not careful, you could leave your devices vulnerable to attacks. Here are some of the most common security risks and how to mitigate them:
- Data Breaches: Use encryption to protect sensitive information and regularly back up your data.
- Unauthorized Access: Implement strong authentication methods and monitor your network for any suspicious activity.
- Malware Attacks: Keep your antivirus software up to date and avoid downloading suspicious files.
Remember, security isn’t a one-time thing. It’s an ongoing process that requires constant vigilance and adaptation.
Tools and Technologies to Enhance IoT Remote Access
There are plenty of tools and technologies out there that can enhance your IoT remote access experience. Here are a few worth checking out:
1. DDNS Services
Dynamic DNS (DDNS) services allow you to access your devices using a domain name instead of an IP address. This makes it easier to remember and manage your connections.
2. Virtual Private Networks (VPNs)
VPNs create a secure tunnel between your device and the internet, protecting your data from prying eyes. They’re a great way to add an extra layer of security to your IoT remote access setup.
3. IoT Management Platforms
Platforms like AWS IoT and Microsoft Azure provide powerful tools for managing your IoT devices. They offer features like device monitoring, data analytics, and remote control, making it easier to manage your smart home.
Case Studies: Real-World Examples of IoT Remote Access
To give you a better idea of how IoT remote access works in the real world, let’s take a look at a few case studies:
Case Study 1: Smart Home Automation
John, a tech enthusiast, wanted to automate his home using IoT devices. He set up a system that allowed him to control his lights, thermostat, and security cameras remotely. By configuring his router’s MAC address and setting up port forwarding, he was able to access his devices from anywhere in the world.
Case Study 2: Remote Monitoring for Businesses
A small business owner used IoT remote access to monitor his store’s inventory and security systems. By implementing a combination of DDNS and VPN, he was able to keep an eye on his business even when he was out of town.
Future Trends in IoT Remote Access
The world of IoT remote access is constantly evolving. Here are a few trends to watch out for:
- Increased adoption of AI and machine learning for device management.
- More focus on security and privacy as cyber threats continue to grow.
- Integration with smart cities and other large-scale IoT projects.
As technology advances, the possibilities for IoT remote access are endless. The future looks bright for those who embrace it.
Conclusion
So there you have it – a comprehensive guide to mastering IoT remote access behind router MAC. By following the steps and best practices outlined in this article, you’ll be able to set up a secure and efficient system that allows you to control your IoT devices from anywhere in the world.
Remember, security should always be your top priority. Stay vigilant, keep your systems updated, and don’t hesitate to reach out for help if you need it. And hey, if you found this article helpful, don’t forget to share it with your friends and leave a comment below. Let’s keep the conversation going!
Table of Contents
- What is IoT Remote Access Anyway?
- Why Router MAC Matters in IoT Remote Access
- Setting Up IoT Remote Access
- Common Challenges and How to Overcome Them
- Best Practices for IoT Remote Access
- Understanding the Security Risks
- Tools and Technologies to Enhance IoT Remote Access
- Case Studies: Real-World Examples of IoT Remote Access
- Future Trends in IoT Remote Access
- Conclusion