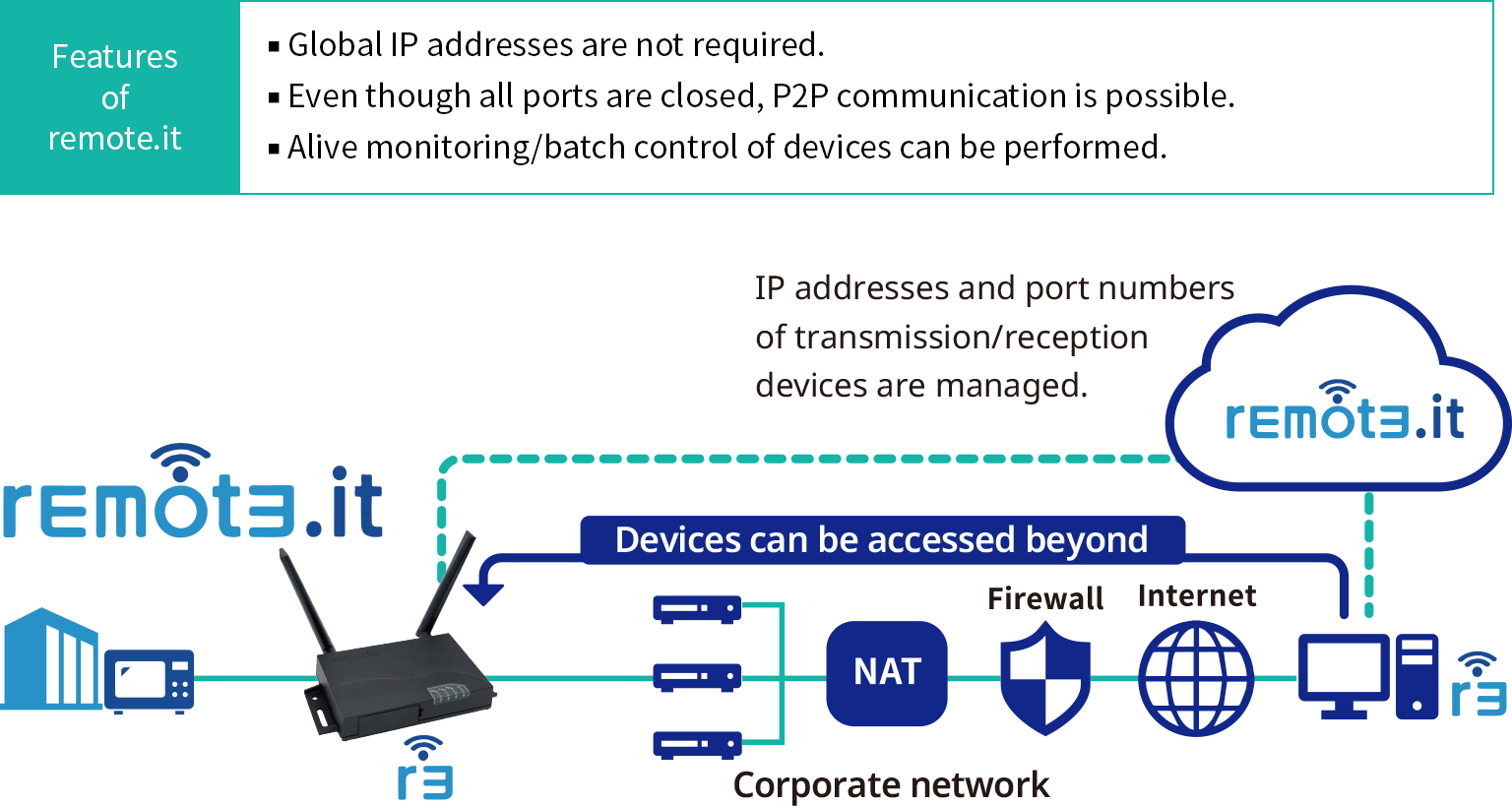
Ever wondered how to control your IoT devices remotely while keeping them safe behind your router? Well, you’re not alone. Millions of people around the globe are diving into the world of smart homes and remote IoT setups, but the question remains—how do you do it without opening yourself up to potential threats? Let’s dive right in!
Whether you’re managing a smart thermostat, checking your home security camera, or automating your lights, remote IoT access is becoming a necessity for modern living. But here’s the catch: doing it wrong can expose your personal data to hackers. So, how do you strike that perfect balance between convenience and security? That’s exactly what we’re going to explore in this guide.
This article isn’t just about tech jargon—it’s about giving you practical steps to set up your IoT devices so they work for you without working against you. If you’re ready to take control of your smart home and keep it safe, let’s get started!
Read also:Reaching Spanishspeaking Customers A Comprehensive Guide For Business Growth
Table of Contents:
- Introduction to IoT and Routers
- Understanding IoT Behind the Router
- Security Risks of Remote IoT
- Setting Up Remote IoT Access
- Using Port Forwarding Safely
- Exploring VPN Solutions
- Leveraging Cloud Services
- Best Practices for IoT Security
- Troubleshooting Common Issues
- Conclusion: Secure Your Smart Home
Introduction to IoT and Routers
IoT—or the Internet of Things—is all about connecting everyday devices to the internet. From smart fridges that tell you when you’re out of milk to doorbells that let you see who’s at your door, these gadgets are designed to make life easier. But here’s the deal: most of these devices are connected to your local network through your router. So, what happens when you want to access them from outside your home?
The router is like the gatekeeper of your network, and it’s designed to keep unwanted traffic out. While this is great for security, it can also make it tricky to access your IoT devices remotely. The good news is that there are ways to bypass this limitation without compromising your safety.
Understanding IoT Behind the Router
What Does "Behind the Router" Mean?
When we talk about IoT devices being "behind the router," we’re referring to the fact that these devices are part of your private network. Your router acts as a firewall, blocking external access by default. This setup is great for protecting your devices from unauthorized access, but it also means you can’t just hop on and control them from anywhere.
Think of it like a fortress. Your router is the wall, and your IoT devices are the treasures inside. If you want to access those treasures from the outside, you need to find a way to get through the wall without tearing it down.
Security Risks of Remote IoT
Why Should You Be Concerned?
Let’s face it—security is a big deal when it comes to IoT. Devices like smart cameras, thermostats, and even baby monitors can become entry points for hackers if not properly secured. When you set up remote access, you’re essentially creating a pathway for potential threats.
Read also:Verizon Fiber Optic Revolutionizing Highspeed Internet For Everyone
Some of the common risks include:
- Data breaches: Hackers can gain access to sensitive information, like your home address or daily routines.
- Device hijacking: Malicious actors can take control of your devices and use them for nefarious purposes.
- Network compromise: A compromised IoT device can open the door to attacks on your entire network.
But don’t worry! There are ways to mitigate these risks, and we’ll cover them in detail later on.
Setting Up Remote IoT Access
Step-by-Step Guide
Setting up remote access for your IoT devices doesn’t have to be complicated. Here’s a step-by-step process to help you get started:
- Identify Your Devices: Make a list of all the IoT devices you want to access remotely.
- Check for Built-In Features: Many modern devices come with apps or services that allow remote access out of the box. Take advantage of these if possible.
- Secure Your Router: Ensure your router’s firmware is up to date and that you’re using a strong, unique password.
- Set Up Port Forwarding: This allows specific ports on your router to direct traffic to your IoT devices.
- Test Your Setup: Use tools like CanYouSeeMe.org to verify that your ports are open and working correctly.
Remember, every router is different, so be sure to consult your router’s manual or manufacturer’s website for specific instructions.
Using Port Forwarding Safely
What Is Port Forwarding?
Port forwarding is a technique that allows external devices to communicate with devices inside your network. By configuring your router to forward specific ports to your IoT devices, you can enable remote access. However, it’s crucial to do this safely.
Here are some tips for secure port forwarding:
- Use non-standard ports instead of common ones (e.g., 8080 instead of 80).
- Limit access to specific IP addresses if possible.
- Enable encryption for any services running on forwarded ports.
While port forwarding can be a powerful tool, it’s not without its risks. That’s why it’s essential to follow best practices and consider alternative solutions like VPNs or cloud services.
Exploring VPN Solutions
Why Use a VPN?
A Virtual Private Network (VPN) creates a secure tunnel between your device and the internet. By using a VPN, you can access your IoT devices remotely while keeping your connection encrypted and private.
Some benefits of using a VPN for IoT include:
- Enhanced security: All data transmitted through the VPN is encrypted, making it much harder for hackers to intercept.
- Privacy: A VPN masks your IP address, making it difficult for anyone to track your online activity.
- Flexibility: You can connect to your home network from anywhere in the world.
When choosing a VPN provider, look for one that offers strong encryption, a no-logs policy, and good performance. Some popular options include NordVPN, ExpressVPN, and ProtonVPN.
Leveraging Cloud Services
How Cloud Services Can Help
Many IoT devices come with cloud-based services that allow for easy remote access. These services handle the heavy lifting for you, so you don’t have to worry about configuring your router or setting up complex systems.
Some popular cloud platforms for IoT include:
- AWS IoT Core
- Google Cloud IoT
- Microsoft Azure IoT
While cloud services offer convenience, they also introduce new security challenges. Make sure to choose a reputable provider and follow their security guidelines to protect your data.
Best Practices for IoT Security
Staying Safe in the IoT World
Here are some best practices to keep your IoT devices secure:
- Change default passwords: Always update the default credentials that come with your devices.
- Keep firmware updated: Regularly check for and install firmware updates to patch security vulnerabilities.
- Use strong encryption: Ensure that all communication between your devices and the internet is encrypted.
- Segment your network: Create a separate network for your IoT devices to isolate them from your main network.
By following these practices, you can significantly reduce the risk of security breaches and enjoy the benefits of remote IoT access without worrying about potential threats.
Troubleshooting Common Issues
Fixing Connection Problems
Even with the best setup, you might encounter issues when trying to access your IoT devices remotely. Here are some common problems and their solutions:
- Device Not Responding: Check that the device is powered on and connected to the network.
- Ports Not Forwarding: Verify your port forwarding settings and ensure that your router’s firewall isn’t blocking the traffic.
- VPN Connection Issues: Try restarting your router and the device running the VPN client.
If you’re still having trouble, consult the documentation for your specific devices or reach out to the manufacturer’s support team for assistance.
Conclusion: Secure Your Smart Home
Remote IoT access is a game-changer for modern living, but it’s important to approach it with caution. By understanding the risks and following best practices, you can enjoy the convenience of controlling your smart devices from anywhere without compromising your security.
We’ve covered a lot in this guide, from setting up port forwarding to exploring cloud services and VPN solutions. Remember, the key to a secure IoT setup is staying informed and proactive. So, take the steps outlined here and make your smart home smarter—and safer.
Now it’s your turn! Have you tried any of these methods? Share your experiences in the comments below, and don’t forget to check out our other articles for more tech tips and tricks. Stay safe out there, and happy IoT-ing!